Procmail is a very general and powerful mail-handling tool. It lets you specify pattern-based rules for your mail, with actions to be taken when the rules match. I use it for a wide variety of tasks, including:
Note that procmail, and any filters you run from procmail, only apply
to single users' mailboxes.
Previous filter layers apply to the entire site, so this is different.
|
ClamAV is very effective but is not perfect. When a new virus pops up, it takes the ClamAV folks hours or days to come out with a pattern to block it. Meanwhile, I don't want those new viruses getting through. I use a small set of procmail patterns that match any Windows executable. This takes more CPU cycles to run than ClamAV, so ClamAV goes first, then this runs as a backup.
:0 B
* ^Content-Transfer-Encoding:.*base64
* ^TVqQAAMAAAAEAAAA
/dev/null
:0 B
* ^Content-Transfer-Encoding:.*base64
* ^TVoAAAAAAAAAAAAA
/dev/null
:0 B
* ^Content-Transfer-Encoding:.*base64
* ^UEsDBAoAAAAAA
/dev/null
:0 B
* ^Content-Transfer-Encoding:.*base64
* ^UEsDBBQAAAAIA
/dev/null
I'm a little uneasy about this filter. Since the patterns are fairly short, they could occasionally match an innocent file by random chance. Perhaps a JPEG sent to me by a friend. What I really ought to do is turn these into local ClamAV patterns, which could be more specific - they could match the magic string only on the first line of the payload, instead of anywhere in the file.
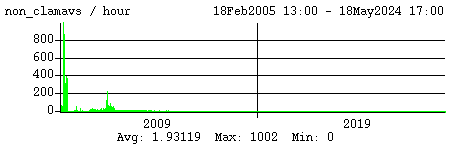
The spike starting on 01May2005 was due to a bug in ClamAV - it was letting certain viruses go through, so this backup measure came into play.
| <<< [ClamAV] <<< | >>> [Bayesian] >>> |
